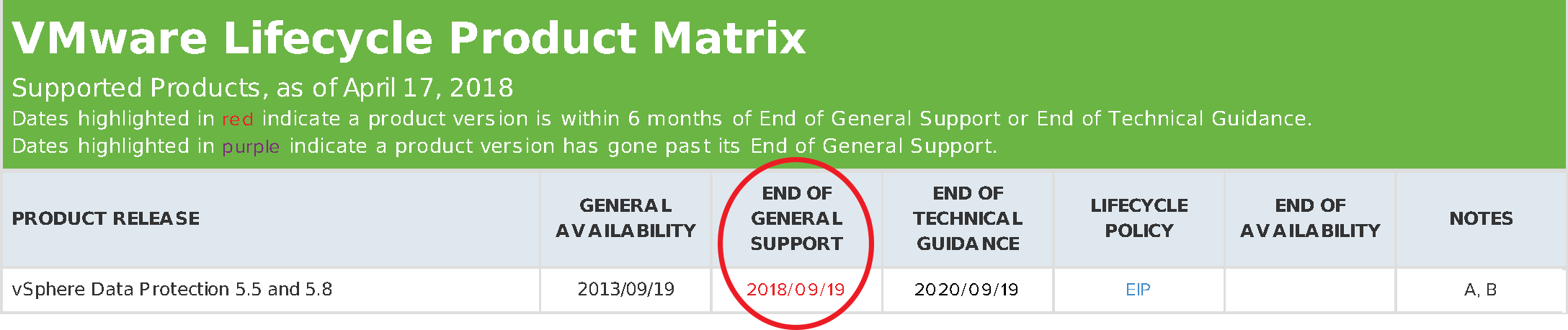
For a 5th time, we're excited to announce that Lewan Technology has been recognized on CRN's 2018 Solution Provider 500 list as one of the top largest technology integrators, IT solution providers and IT consultants in Denver, Colorado and North America.
The SP500 list is the predominant channel partner award list, serving as the industry standard for recognition of the most successful solution provider companies.