Proactively plan for threats and risks by assessing and mitigating security and business concerns using a mix of technologies and automation, training and policies.
We don’t use scare tactics to try to sell you security technologies or services you don’t need. We take a step back with you and look at your business situation, your compliance requirements, the security threats and business risks you face, and your security stance to develop an approach that’s a custom fit.
Infrastructure Security Management
 Highly secure firewall, web and email services to enable secure access whether working in the office, mobile or remote. You could go out and buy a network security solution off the shelf, but what you get out-of-the-box is a one-size-fits-all product that doesn’t know your unique business security challenges. We’ll work with you to identify, design and implement a custom, right-sized security policy and solution for your business.
Highly secure firewall, web and email services to enable secure access whether working in the office, mobile or remote. You could go out and buy a network security solution off the shelf, but what you get out-of-the-box is a one-size-fits-all product that doesn’t know your unique business security challenges. We’ll work with you to identify, design and implement a custom, right-sized security policy and solution for your business.
- Lewan has Passed the SSAE 18 SOC 2 Type II Audit
- Advanced Malware Protection (including Ransomware like CryptoLocker)
- Web Security
- Email Security (including Phishing, SPAM)
- Endpoint Security Clients
- Access Control and Policies
- Firewalls
- VPN
- Network Security
- Next Generation Intrusion Prevention System (IPS)
Infrastructure Security Assessments
Security assessment to help ensure your place of business is as secure as possible. Are you sure your network, servers and IT environment is secure? We can test it to ensure that network equipment, servers, desktops are properly configured. We can review or help build policies and procedures that help ensure your business is running as securely as it needs to be.
- Security Assessments
- Penetration Testing
- Vulnerability Assessment
- Security Incident Response
Infrastructure Risk Management
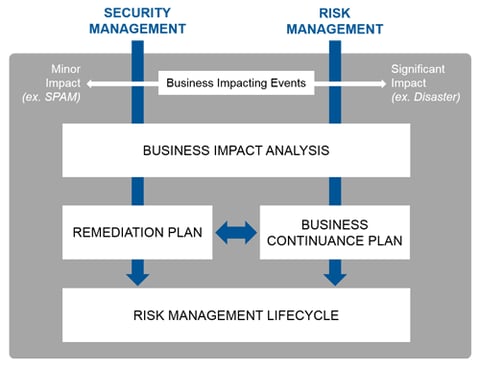 A comprehensive, business-focused approach to Risk Management; not just a mix of security point solutions. Starting with the impact on your business of malware attacks to outages of critical business applications, we develop plans to mitigate the most applicable risks and implement policies, training, and technology solutions…leading to a well-rounded, business-focused approach. We use an industry standard lifecycle to guide you through a solid Risk Management program.
A comprehensive, business-focused approach to Risk Management; not just a mix of security point solutions. Starting with the impact on your business of malware attacks to outages of critical business applications, we develop plans to mitigate the most applicable risks and implement policies, training, and technology solutions…leading to a well-rounded, business-focused approach. We use an industry standard lifecycle to guide you through a solid Risk Management program.
- Business Impact Analysis. Applicable business impacting events, business risk and impact. Includes analysis of your risk and security approach to determine compliance against the applicable standards, including ISO 27001, NIST 800-53, SANS 20, FFIEC, HIPAA, PCI, or your own company-mandated compliance.
- Security Remediation Plan. Customized security-focused initiatives mapping to the business risks identified.
- Business Continuance Plan. Customized business continuance planning to answer “how do we operate as a business in the case of a major computer or network outage?”
- Disaster Recovery Plan. Often a subset of the Business Continuance Plan, a DR plan helps prepare for the IT aspects of a major outage.
- Training. End user training to raise awareness of the risks and methods being used by today’s “hacker”, and technical training and knowledge transfer for those on your team tasked with security.
- Policy and Procedure Development. Ranging from security polices used by your HR department for PII (Personally identifiable information) to procedures to be enacted upon a disaster being declared.
Ongoing monitoring, management, and support to proactively identify and act upon security issues and technology related risks. Today’s broad range of security incidents elicits the need for automated monitoring, management and response that’s even more broad and diverse. In addition, the cost of downtime continues to increase with increasing reliance on technology. We can help you implement your own security and risk management approach or provide it to you as a service.
- Vulnerability Management
- Breach Detection
- Incident Response
- Behavioral Monitoring
- SIEM (Security Information and Event Management)
- Security Equipment Monitoring and Management
- Disaster Recovery as a Service (DRaaS)
- Managed Data Protection (Backup)