Cisco has disclosed an Adaptive Security Appliance (ASA) Remote Code Execution and Denial of Service vulnerability that could affect your Cisco ASA and Cisco Next-Generation Firewall platforms.
The vulnerability, CVE-2018-0101, will allow a malicious individual to send specially crafted XML to your device and have it reboot or stop processing VPN traffic. This attack is currently being used and is not limited to the lab environments.
Craig Williams, a Cisco researcher and director of outreach for Cisco's Talos security team confirmed:
This is not a drill..Patch immediately. Exploitation, albeit lame DoS so far, has been observed in the field https://t.co/2IlBkisKex
— Craig Williams (@security_craig) February 9, 2018
The vulnerability is due to allocating and freeing memory during the processing of the malicious XML payload. In the lab, this has also been shown to allow remote code execution to take over a device. As of yet, no one has reported a successful take over in the real world. Even so, it’s critical to patch your devices using this advisory documentation: Cisco Adaptive Security Appliance Remote Code Execution and Denial of Service Vulnerability
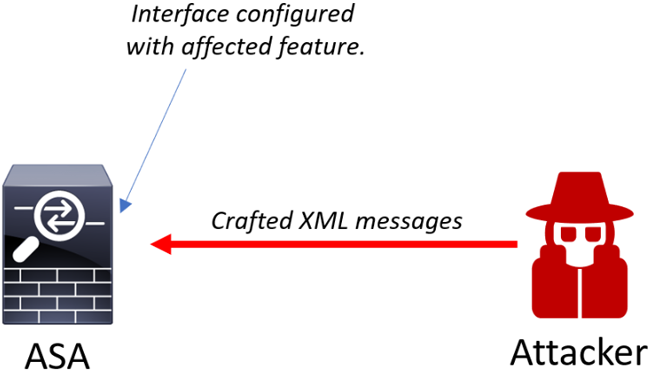
Photo Credit: Cisco
This vulnerability affects Cisco ASA Software that is running on the following Cisco products:
- 3000 Series Industrial Security Appliance (ISA)
- ASA 5500 Series Adaptive Security Appliances
- ASA 5500-X Series Next-Generation Firewalls
- ASA Services Module for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series Routers
- ASA 1000V Cloud Firewall
- Adaptive Security Virtual Appliance (ASAv)
- Firepower 2100 Series Security Appliance
- Firepower 4110 Security Appliance
- Firepower 4120 Security Appliance
- Firepower 4140 Security Appliance
- Firepower 4150 Security Appliance
- Firepower 9300 ASA Security Module
- Firepower Threat Defense Software (FTD)
- FTD Virtual (FTDv)
Fixed release versions are:
| Cisco ASA Major Release | First Fixed Release |
| 8.x1 | Affected; migrate to 9.1.7.23 |
| 9.01 | Affected; migrate to 9.1.7.23 |
| 9.1 | 9.1.7.23 |
| 9.2 | 9.2.4.27 |
| 9.31 | Affected; migrate to 9.4.4.16 |
| 9.4 | 9.4.4.16 |
| 9.51 | Affected; migrate to 9.6.4.3 |
| 9.6 | 9.6.4.3 |
| 9.7 | 9.7.1.21 |
| 9.8 | 9.8.2.20 |
| 9.9 | 9.9.1.2 |
1 ASA Software releases prior to 9.1, including all 8.x releases, and ASA releases 9.3 and 9.5 have reached End of Software Maintenance. Customers should migrate to a supported release.
If you’re unsure how vulnerable your company is to this Cisco exploit, need help patching, or you want to work with a managed security provider to ensure you are secure,  for a consultation to see how we can protect your business, your end users and your customers from a network take down.
for a consultation to see how we can protect your business, your end users and your customers from a network take down.