The “Internet of Things”, or IoT for short, is a buzzword you’ve probably heard many times before, but what does it really mean? Simply put, an IoT product is just a sensor with the ability to call home and execute functions that it’s designed for.
It’s become a hot topic in the last decade, but IoT has actually been around much longer than that even. One of the first mainstream consumer-facing applications was implemented in 1982. It was a smart Coca-Cola vending machine that reported the status of the vending machine so a technician could be sent to refill the cans when it was running low. If we fast forward to 2020, researchers predict 30-50 BILLION devices will be connected. By comparison, that’s 4-7x the world’s population.
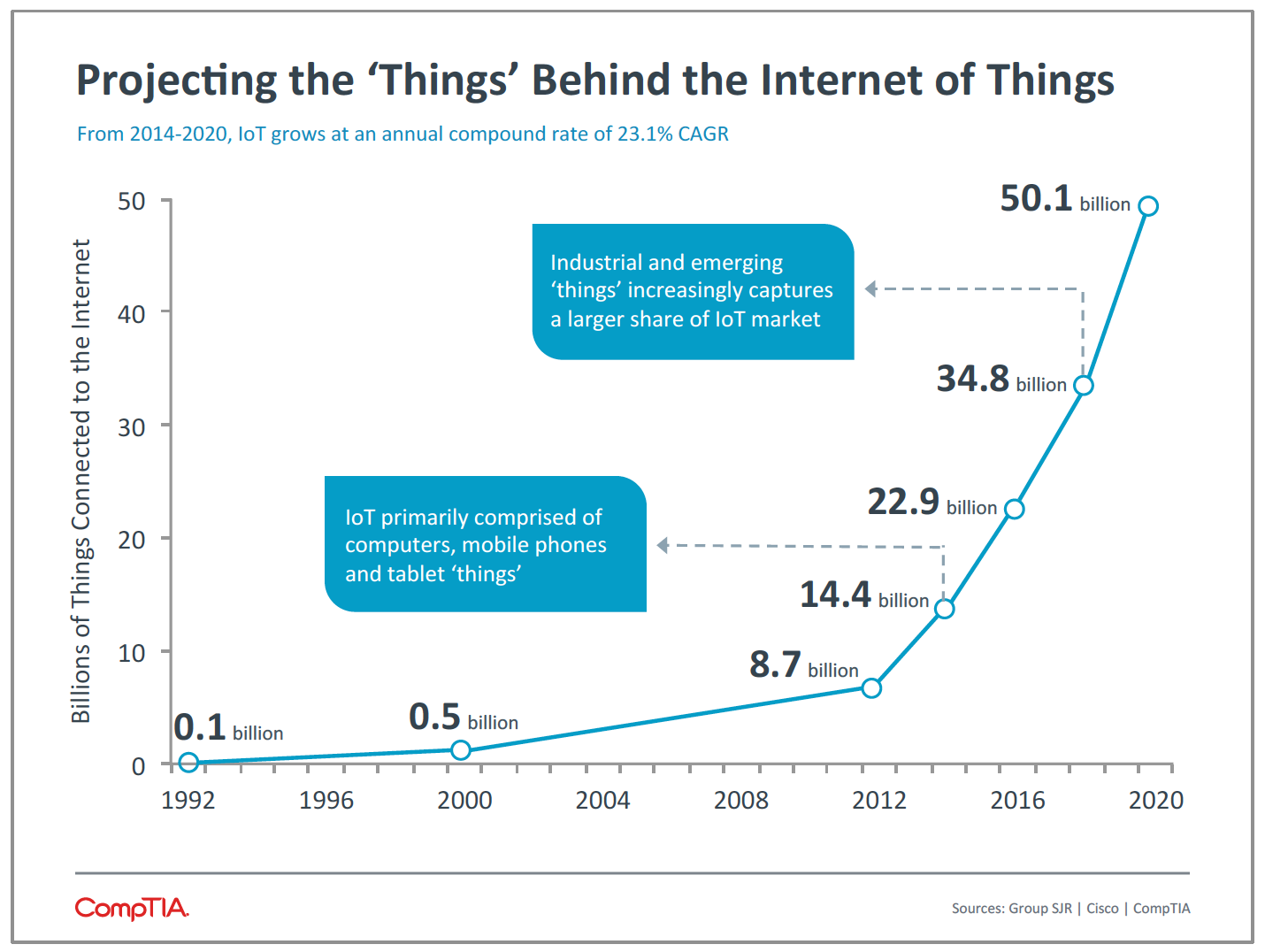
Credit: CompTIA
Today a whole suite of consumer IoT products exist from Google Home and Amazon’s Alexa to connected cars, garage doors, sprinkler systems, coffee machines, stoves, cameras, lightbulbs, dishwashers refrigerators, vacuum cleaners, air purifiers, etcetera, etcetera.
These products make our lives easier and more efficient, but don’t let convenience take precedence over privacy and security. We often forget to think about security, like we do with our cell phones or computers, when it comes to these other devices.
Malware writers could hack into any of these IoT devices to see if you are home or listen to your conversations to figure out when you’re going to be out of town. We don’t have control over how well manufacturers have embedded security into hardware or software, but we can control how the device connects to our network.
This becomes even more critical for organizations with complex networks, smart offices and the general unavoidability of IoT in today’s business environments.
I’m not here to scare companies away from embracing IoT. It’s a way they can be closer to their clients and provide better service by creating feedback loops through IoT sensors. It changes the way businesses function for the better, shifting the focus from products to utility and service.
So as a business, how do you make sure your network and IT team is ready for these connected devices?
Here are 6 steps to get you started:
- Capacity and Scale. Make sure your network is ready for the additional IoT devices from a load-bearing stand point. From thermostats, to IP cameras, badge scanners, electric charging stations and lights—the number of connected devices can outgrow the capacity of your network quickly so it’s important to plan your wireless and wired network appropriately. Wireless technologies based on 11ac Wave 2 today and 802.11ax for the future can support such densities of devices without taking a toll on performance. If wired, make sure enough port capacity is accounted for.
- Access Control. Only legit IoT devices that your IT department supports should be able to connect to the network. Device profiling with access control solutions can be of great help. Identity services engine (ISE) from Cisco is a widely used and adopted network access control (NAC) solution for wired and wireless access. Check out this short video that makes ISE easy to understand:
- Asset Tracking. You can’t protect things that you don’t know exist. A process should be defined for employees that requires them to contact their IT department before connecting a new device to the network so it can be vetted and authorized properly. ISE can help prevent rogue devices from connecting, or even if already connected, separate safely from the corporate network. ISE can also help with the asset tracking of devices on the network.
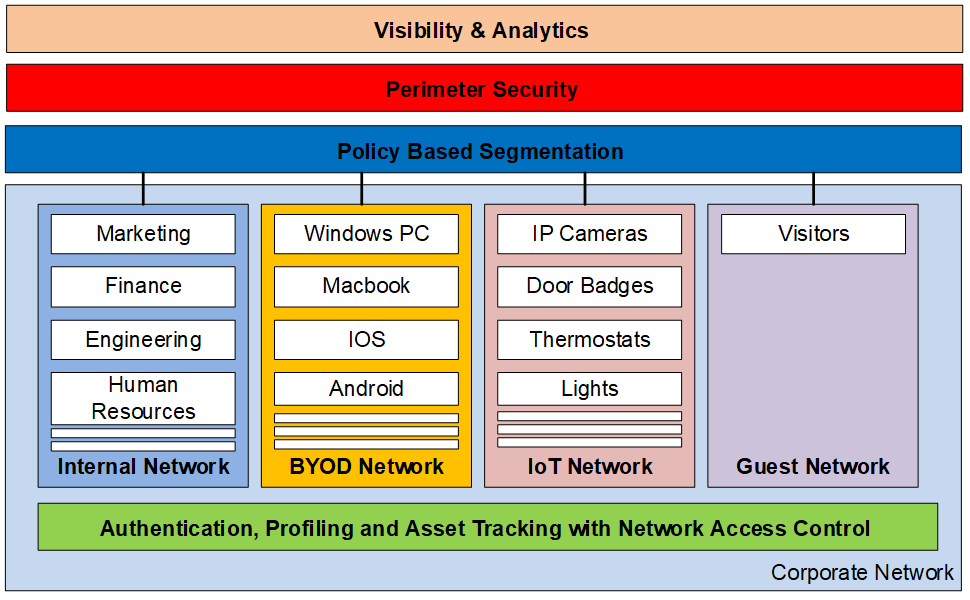
- Policy-Based Segmentation. For every non-traditional device connected to your network, you’ve got one more access point for a potential hack. You can’t install traditional anti-virus and host scanning software on these devices like you can on Windows, Mac, Android or iOS machines. It’s important to segment such devices from your corporate or critical networks to contain the impact if there is a breach. The most basic technique is using virtual local area network (VLAN) segmentation but VLANs can quickly get complicated with scale. Software-defined (SD) solutions like Cisco’s SD-Access use secure group tags (SGTs) instead of VLANs plus ISE to automate access control to/from the IoT networks.
- Securing the Perimeter. Your IoT network needs protection from the outside world and malware just like your internal networks do. Firewalls with intrusion detection, protection (IDS/IPS) and advanced malware protection (AMP) should be inserted between the IoT network and the internet. Additionally, DNS layer protection like Cisco Umbrella should be utilized as a first line of defense to stop attacks.
- Visibility and Analysis. After all of the above steps are taken, you have essentially secured your IoT network. But it’s also important to inspect network traffic in real-time for anomalies, emerging day-zero threats and compromised hosts. This will help you detect attacks that get past your segmentation and perimeter defenses. Lewan’s Advanced Security Services can assist in this area.
Network security can be a big undertaking, but is also mission critical.  to learn more about our Advanced Security Services. Our team of experts can help you understand risks associated with IoT, assist with design and deployment of the appropriate network architecture and protections. We can also help develop an incident response plan to maintain services resiliency and achieve business continuity.
to learn more about our Advanced Security Services. Our team of experts can help you understand risks associated with IoT, assist with design and deployment of the appropriate network architecture and protections. We can also help develop an incident response plan to maintain services resiliency and achieve business continuity.