We've been building our next generation security practice at Lewan for over a year now and I’ve learned more than I ever knew about the space before we started. Our new team of Security Analysts run our Security Operations Center (SOC) and provide over-watch for our Network Operations Center (NOC). These teams take security seriously for our clients who take security seriously.
With this have come a lot of best practices and insights. Here are two main points that I hope you’ll find helpful when looking for a managed security service provider.
Intrusion Prevention vs. Advanced Monitoring and Management
Ideally, you want a partner that’s going to set you up with an impenetrable firewall and all of the latest intrusion prevention technologies. But what if a threat gets past this barrier and no one is watching because they aren’t expecting a breach?
It amazes me what we find on the networks we monitor—even with firewalls and intrusion prevention in place.
For your security measures to be truly secure, you need a provider that is going to monitor and manage your network 24/7 to catch those newer-than-the-newest-patch intrusions that infiltrate your system before they can sink their teeth in and do the real damage.
The example below is just another day on one of our networks that has a full suite of defensive measures in place (firewalls, intrusion prevention, email security, next generation endpoint protection, web filtering…the list goes on). And our detection services are still finding flagged risks.
The good news is that many of these “threats” may be passive. Advanced machine learning and correlation aren’t going to weed these out though, a human needs to complete an analysis to dismiss or escalate these risks.
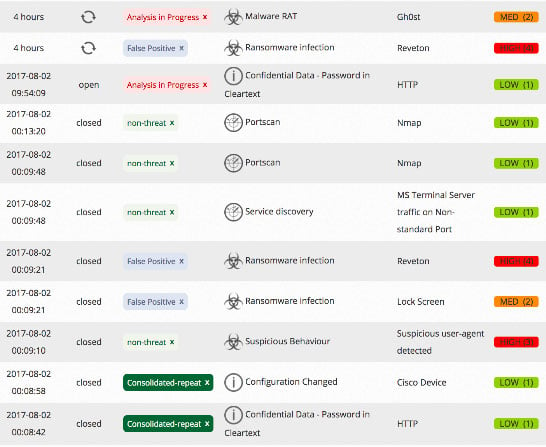
Our analysts grab these alarms as they come through, work through the OODA loop, label and close once resolved.
Customized Levels of Support
One size security does not fit all. You should have the option select the amount of support you need based on how you want your provider to assist your IT team.
Here’s how we do it. This is also good insight into how security management is usually broken up so you know what to look for and ask for when vetting any managed security provider.
The names we use for our segments are Defend, Detect and Comply.
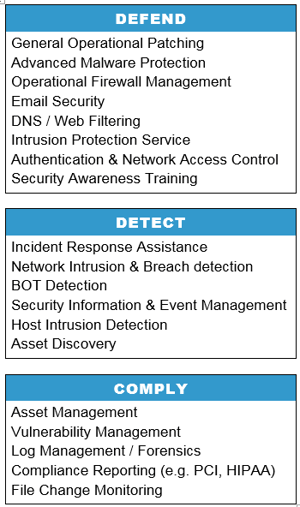
Defend
Think of home security – what preventative measure are you going to take first? Locking your doors and windows or hiring a 24x7 security guard?
Locking up obviously is the first line of defense against burglars. In the same way, defend services are the foundation. Before you can start detecting intrusions or complying with policies, you have to have something in place to keep most of the bad stuff out.
We help clients understand their defense posture and implement solutions to help them stand up these defense mechanisms. Then we can manage them over time if the client wants to use our managed services to have us keep an eye on their defense technology and monitor and remediate issues we find.
Detect
Once a defense is implemented and being managed, we can layer on detect services which adds an additional layer of tools, processes and people (our SOC) to perform 24x7 monitoring with daily log reviews to detect any potential activity happening behind the defense mechanisms. These tools provide asset discovery, security information, event management, event correlation utilizing the open threat exchange, and vulnerability management. Our security analysts then use the OODA loop process to analyze and act on these alarms notifying our NOC, who is managing the defense systems.
Comply
For clients who have compliance needs we can add on ala carte reporting, scheduled vulnerability scanning, file integrity monitoring and log management to help with compliance and auditing processes.
I hope this insight into how we do Advanced Managed Security Services helps you better understand the offering, whether through us or another provider.  for a consultation to see how we can protect you and your end users from data, email, internet and mobile security threats.
for a consultation to see how we can protect you and your end users from data, email, internet and mobile security threats.