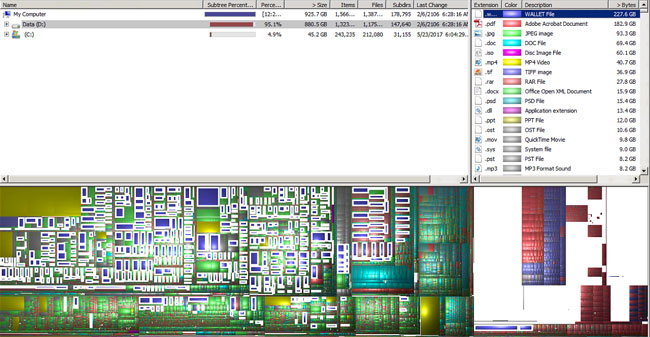
Guest post by Lewan Solutions Architect Priyank Ghedia.
Cisco Live is one of the most awaited events every year for networking enthusiasts. This year the conference returned to Las Vegas, June 25 – 29 with some impressive stats: 28,000 attendees , 3,000 speakers and 1,000 education sessions.
There was something for every type of IT professional with sessions on Border Gateway Protocol (BGP), firewalls, data center architectures, cloud security plus opportunities to talk to industry specialists, peers and networking experts.